Autonomous AI That Investigates Every Alert
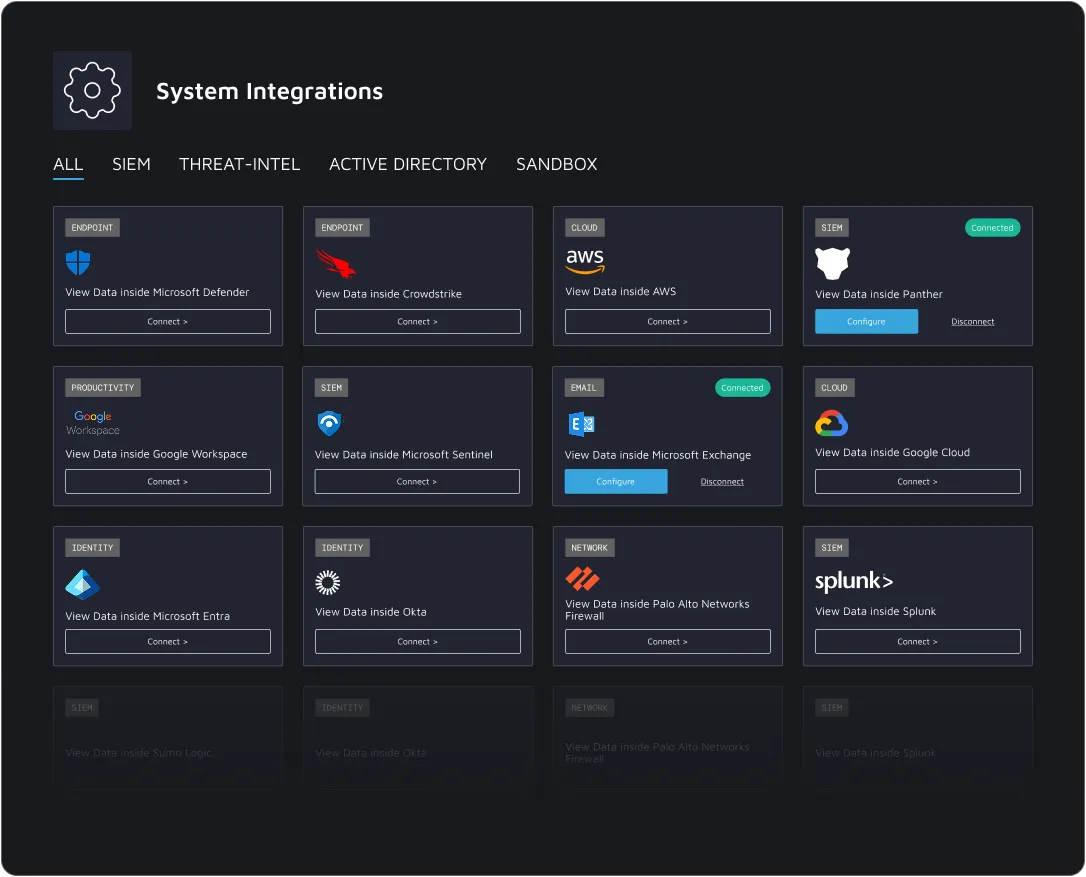
Pre-trained on 70+ security tools

Investigate
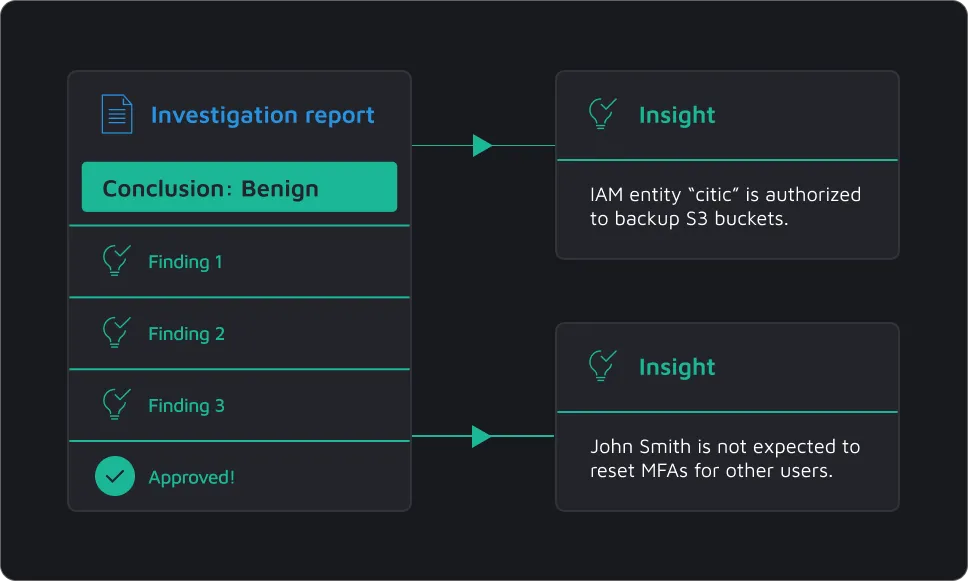
As soon as Dropzone AI receives an alert, it begins an investigation—replicating expert analyst techniques and using multiple tools and data sources to gather evidence. If needed, it can even interview affected users to confirm details and clarify intent.
Adapt
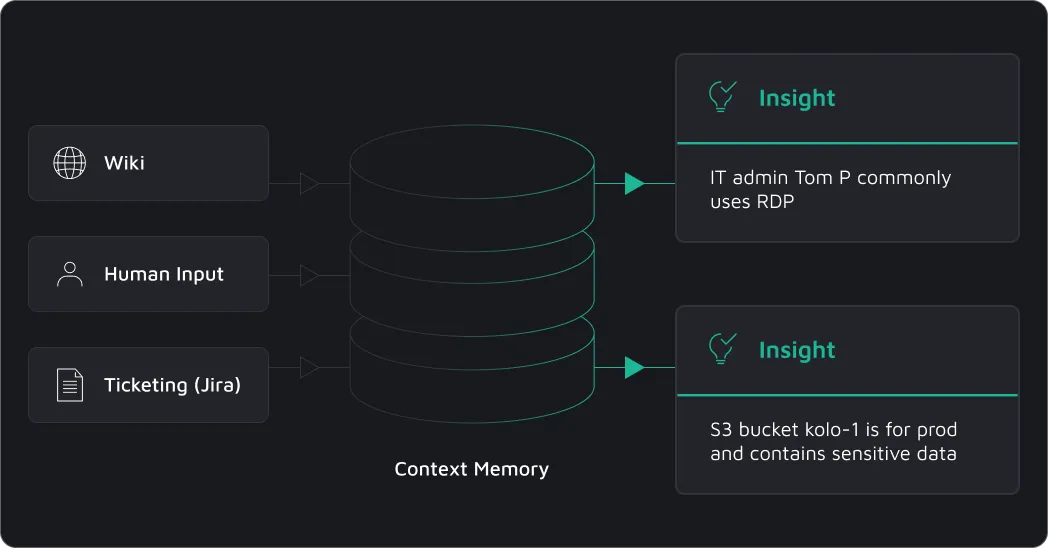
Dropzone AI learns your environment through continuous investigations and feedback. It understands your policies, risk tolerance, and workflows, adapting its behavior accordingly. You can guide its actions to align precisely with your SOC procedures.
Contain
When an investigation concludes, Dropzone AI takes the right action—dismissing false positives, notifying your team, escalating credible threats, or containing incidents to prevent further damage. Every response is informed by the full investigation context.
A tier-1 SOC analyst always in the zone.






















































How It Works
SOC Integration & Secure Deployment Architecture

Frequently Asked Questions
Dropzone AI is an autonomous AI SOC Analyst that investigates security alerts, mimicking the reasoning process of expert analysts. It triages alerts, correlates data, and provides decision-ready reports—helping SOC teams reduce manual investigation time and improve security response efficiency.
Dropzone AI seamlessly integrates with SIEM, SOAR, EDR, and cloud security tools like Splunk, CrowdStrike, Microsoft Defender, and AWS Security Hub. It ingests security alerts from these platforms, enriches them with context, and autonomously performs full investigations to reduce analyst workload.
Yes, Dropzone AI uses large language models (LLMs) and contextual memory to filter out false positives. By analyzing security logs, correlating alerts, and applying investigative reasoning, it reduces noise and ensures security teams focus on real threats.
Dropzone AI can investigate security alerts in minutes, compared to the hours it takes human analysts. By automating repetitive tasks and applying recursive AI reasoning, it dramatically shortens Mean Time to Resolution (MTTR) and helps SOC teams respond faster to threats.
Yes, Dropzone AI is scalable for both small security teams and large enterprises. It allows small teams to extend their capabilities without hiring more analysts, while enabling large enterprises to manage high alert volumes with AI-driven investigations.
Unlike traditional SOAR platforms that require playbooks and manual configurations, Dropzone AI autonomously investigates security alerts using advanced reasoning. It goes beyond rule-based automation by dynamically collecting evidence, analyzing context, and providing security teams with AI-driven insights, reducing manual workload and improving threat response efficiency.



-1.webp)







