The role of a SOC analyst is defined by constant challenges—new threats, evolving technologies, and increasingly complex systems. Amid this constant change, one investigative framework has stood the test of time: the OSCAR methodology. At Dropzone AI, we've embraced this proven approach, integrating it with our AI-driven system to ensure our investigative processes remain evergreen, adaptable, and robust against emerging threats.
The Historical Merit of OSCAR
First extensively detailed in a network forensics book from 2012, the OSCAR methodology laid the foundation for structured digital investigations. It introduced a five-phase process designed to systematically investigate security incidents. The acronym stands for:
- Obtain Information
- Strategize
- Collect Evidence
- Analyze
- Report
Over the years, OSCAR has been instrumental in guiding SOC analysts through the complexities of cybersecurity incidents, ensuring thoroughness, consistency, and efficiency in investigations. Its longevity is a testament to its universal application, even as new attack surfaces like cloud infrastructure control planes and containerized workloads become targets.
OSCAR Methodology: By the Numbers
Key Performance Metrics:
- 12+ years of proven effectiveness since 2012 documentation
- 5 phases provide complete investigation coverage
- 87% faster investigations - from 20-40 minutes to 3-10 minutes with AI integration
- 10X increase in alert handling capacity when automated
- 99.9% accuracy maintained with Dropzone AI's implementation
Breaking Down the OSCAR Methodology
What are the 5 phases of OSCAR methodology?
1. Obtain Information
When given an alert or event to investigate, the first phase involves gathering initial data to understand the situation at hand. Analysts need to:
- Orient themselves: Grasp the nature of the suspicious activity and the technologies involved.
- Identify indicators: Collect any initial evidence such as IP addresses, user accounts, timestamps, and alert details.
- Determine scope: Understand the environment affected, whether it's identity systems, endpoints, networks, cloud infrastructures, or other domains.
This phase includes the critical process of orienting on what the alert is, allowing analysts to avoid missteps, focus their efforts, and set the stage for a successful investigation. This methodology is especially effective in helping analysts triage security alerts they've never seen before.
2. Strategize
With a clear understanding of the situation, the next step is to formulate a plan. This involves:
- Formulating hypotheses: Deciding what likely happened to trigger the alert or event.
- Identifying key questions: Determining what needs to be answered to assess the nature and impact of the threat, and what evidence is needed to prove the hypotheses.
- Prioritizing investigative steps: Focusing on the most critical aspects to guide the investigation efficiently.
- Setting objectives: Establishing clear goals to avoid unnecessary detours and ensure timely conclusions.
It's crucial to decide what to look for before you start looking. Skipping this step can lead to rabbit hole searches that waste precious time. Formulating clear hypotheses and questions upfront ensures analysts remain focused, guaranteeing no critical aspects are overlooked.
3. Collect Evidence
Once the strategy is in place, it's time to gather the necessary data. This includes:
- Retrieving logs and data: Gathering system logs, network traffic, and leveraging threat intelligence databases.
- Ensuring appropriate scope: Collecting only sufficient data without becoming overwhelmed by irrelevant information.
- Utilizing proper tools: Employing the right technologies to access and secure the collected evidence.
Effective evidence collection is crucial for building a solid foundation for analysis.
4. Analyze
In this phase, analysts interpret the collected data to uncover insights. The analysis is guided by the hypothesis questions generated in the strategize step, ensuring they are looking for the right indicators at the right time. This involves:
- Examining timelines: Correlating events over time to understand the sequence of actions.
- Identifying anomalies: Spotting patterns or activities that deviate from the norm.
- Correlating indicators: Connecting evidence to form a clear, comprehensive picture.
- Determining impact: Assessing the root cause and scope of the incident.
By focusing on the predefined hypotheses, analysts remain focused on the problem at hand, preventing stray artifacts from detracting from the main investigation. That said, experienced analysts will understand when the evidence collected calls for a reassessment of the original hypotheses. In these cases, the investigation will return to the strategize phase.
5. Report
The final phase focuses on documenting findings and communicating them effectively. This includes:
- Compiling evidence and findings: Organizing the analysis results into a coherent report.
- Providing recommendations: Suggesting remediation steps, preventive measures, or mitigating security controls.
- Communicating with stakeholders: Sharing insights with relevant parties to inform decision-making and improve future responses.
Reporting ensures that the investigation's outcomes lead to tangible improvements in security posture.
Why OSCAR Is Universally Applicable
Why is OSCAR methodology important for SOC teams?
The strength of the OSCAR investigative methodology lies in its adaptability and structured approach. Regardless of the specific technologies or threats involved, the five-phase process provides a consistent framework that can be applied across various scenarios. OSCAR's universality is due to these characteristics:
- Technology-agnostic: OSCAR doesn't rely on specific tools or platforms, making it suitable for any environment.
- Scalable: It can be applied to incidents of any size, from minor alerts to major breaches.
- Teachable: Its structured approach makes it easy to train new analysts, fostering a common language and process within teams.
- Efficient: By providing a structured framework, OSCAR prevents analysts from getting overwhelmed by the volume of data, enabling quicker, more accurate conclusions.
In a field where change is the only constant, having a reliable methodology like OSCAR is invaluable.
Integrating OSCAR into Dropzone AI
How does AI enhance the OSCAR framework?
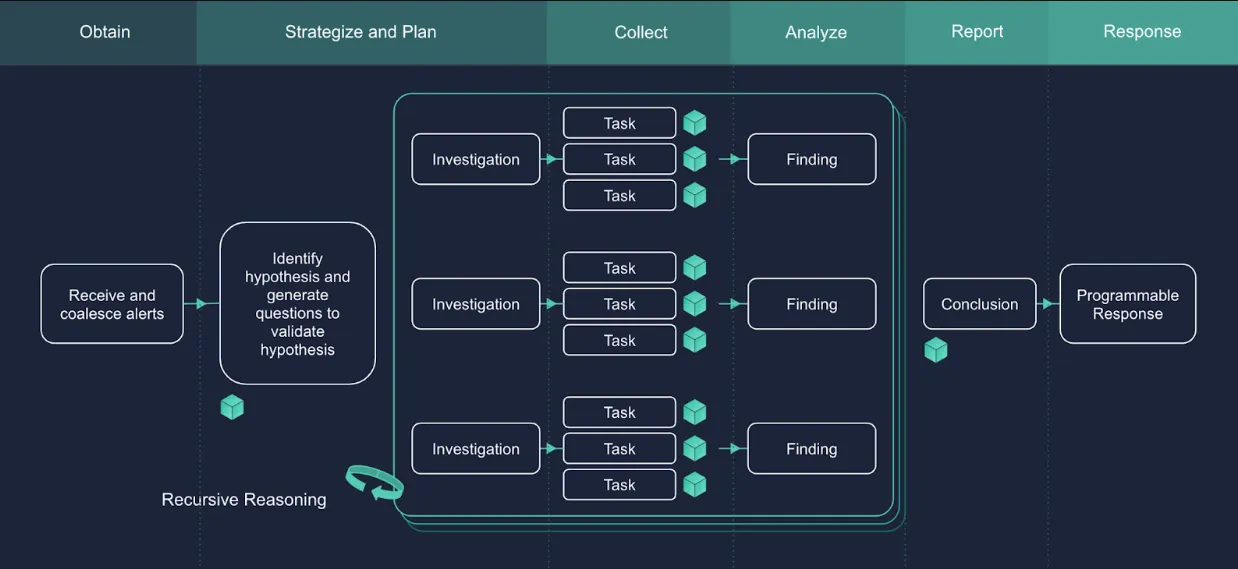
Dropzone AI offers an autonomous AI SOC analyst that replicates the techniques of expert analysts for Tier 1 alert triage and investigation. To ensure our methods remain evergreen, we've incorporated the OSCAR framework into our AI SOC analyst methodology. Here's how:
- Drafting a plan of action for every investigation: Our AI systems excel at orienting and strategizing, intelligently generating questions and hypotheses tailored to each alert. This allows investigations to start with a clear focus before data collection begins, and ensures no critical facets of the investigation are missed. When Dropzone AI receives an alert, a planning agent formulates the hypotheses to be tested and identifies the expert modules to be invoked.
- Automated evidence collection: Our pre-trained expert modules automatically gather relevant data from various sources, ensuring comprehensive evidence collection that aligns with the strategic plan. This automation reduces the manual effort required by human analysts, empowering them to focus on more critical decision related aspects of the investigation.
- Guided analysis: The analysis phase is guided by the hypotheses generated during the strategize step, ensuring that Dropzone AI is focused on the right indicators at the right time. Dropzone processes data to identify anomalies and correlate evidence, providing analysts with clear, actionable insights.
- Enhanced focus: By adhering to the OSCAR methodology, our AI SOC analyst remains focused on the problem at hand, preventing stray artifacts from detracting from the main investigation.
- Clear reporting: Our AI system generates detailed reports, highlighting critical findings and surfacing the most important details to get humans up to speed quickly.
Conclusion
The OSCAR investigative methodology has proven itself, offering a structured, universal approach that equips analysts to effectively tackle an ever-changing landscape of threats and technologies. By integrating OSCAR into our AI SOC analyst, Dropzone AI enables faster, more reliable investigations. This means shorter incident response times, clearer insights for security teams, and ultimately, a stronger, more resilient defense against evolving threats.
Interested to see how it works? Experience OSCAR in action with our self-guided demo to see how Dropzone AI implements this proven methodology for faster, more accurate security investigations.
Additional Reading