Introduction
Security Operations Centers (SOCs) face constant challenges, from managing endless alerts to addressing visibility gaps, often leading to missed threats and breaches. To improve efficiency, SOCs must focus on the 3 Cs: Context, Coverage, and Communication. Coverage is the biggest challenge among these, as gaps often cause incidents to go unnoticed. This article explores the 3 Cs, focusing on how AI will dramatically increase coverage for SOCs, drawing insights from Caleb Sima’s BSides SF 2024 talk, Unlocking the Future: AI is the Key to CISOs Top Challenges.
The 3 Cs Defined
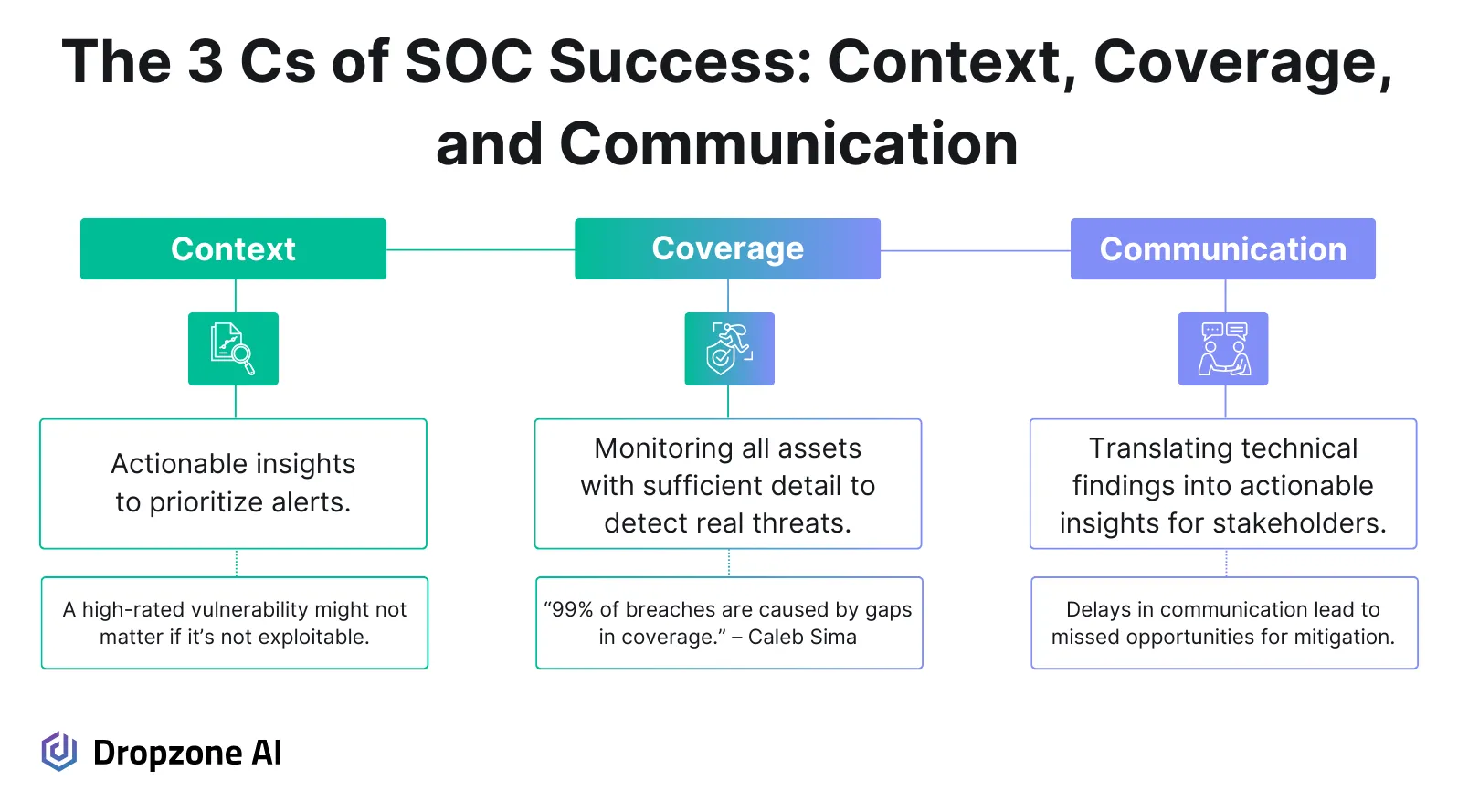
Context
Context is about giving security teams the right insights to understand and prioritize alerts. For instance, a “high” severity vulnerability might seem urgent, but it's not worth immediate attention if it can’t be exploited in your environment.
Analysts can waste valuable time chasing non-critical issues without proper context instead of focusing on real threats. Good context helps teams stay focused and work smarter.
Coverage
Coverage means monitoring everything in your environment while keeping enough detail to spot real threats. Caleb Sima put it best when he estimates: “gaps in coverage cause 99% of breaches.” Problems like shadow IT (untracked systems or assets) and missing log data create blind spots that attackers can easily exploit.
Take the instance of an unmonitored AWS bucket or missing object-level logs that could allow unauthorized access to slip through unnoticed. Coverage is the foundation for both context and communication. Without it, SOCs can’t fully understand threats or communicate their findings effectively. Ensuring there are no gaps in monitoring allows teams to act confidently and build a stronger security posture.
Communication
Communication means turning technical findings into actionable insights for different audiences, like executives, engineers, or external teams. If those findings aren’t clear, decisions can be delayed, and priorities can get misaligned. Good communication ensures everyone is on the same page so the SOC can act quickly and keep threats under control.
Coverage: The Core SOC Challenge
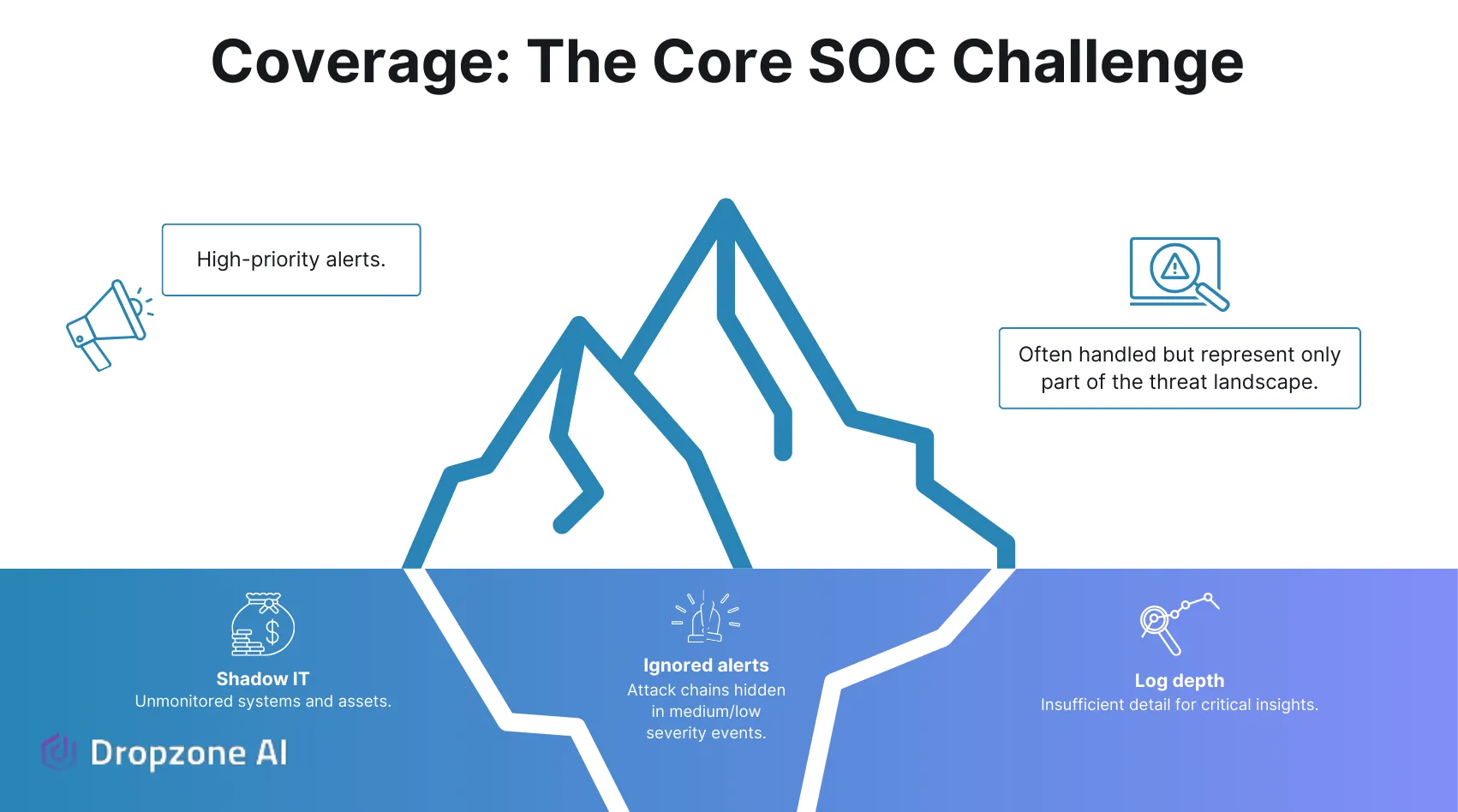
The Problem with Coverage
Coverage gaps in the SOC are one of the main reasons incidents get missed. First, you need width of coverage, meaning that you see a lot of assets and activity in your environment. Unmonitored assets, like an AWS bucket that isn’t being tracked, can become easy targets for attackers. Second, you need depth of coverage, or details that allow your team to dig into what really happened. Incomplete logs or missing details, like object-level access, make it even harder to spot and investigate unusual activity.
Alert triage is also a coverage issue. Medium and low-severity alerts are often ignored because teams lack the time or resources to investigate them. Attackers take advantage of this by hiding malicious actions in what look like routine activities. These less urgent alerts might not seem important individually, but they can form the building blocks of a larger attack. Without the ability to investigate these alerts, real threats can get missed.
Impact of Poor Coverage
Missing coverage creates serious risks for SOCs. To illustrate this, say you had an unmonitored S3 bucket without proper logging that exposed sensitive information like access keys. First, you would want to know why this happened despite having Service Control Policies in place. Second, you would want to know if that sensitive data was accessed, and by whom. These are issues that coverage addresses. Another example would be when software applications keep track of login failures, but don’t track successful logins. That means you can’t detect brute-force attempts.
Alert triage is the most obvious example of the coverage problem. Caleb Sima explained in his session, “We all know that attacks happen through a combination of medium and lows … It's highly likely that in most attacks, you actually saw it—the event was there, it's just no one looked.” In other words, SOCs often only see isolated events, like an anomalous access alert, but don’t have time to fully investigate those and piece together a full picture of what is actually a serious incident. Coverage gaps in alert investigation prevent SOCs from understanding the full chain of events, preventing them from effectively responding or preventing similar incidents from occurring again.
How AI Fixes the Coverage Problem
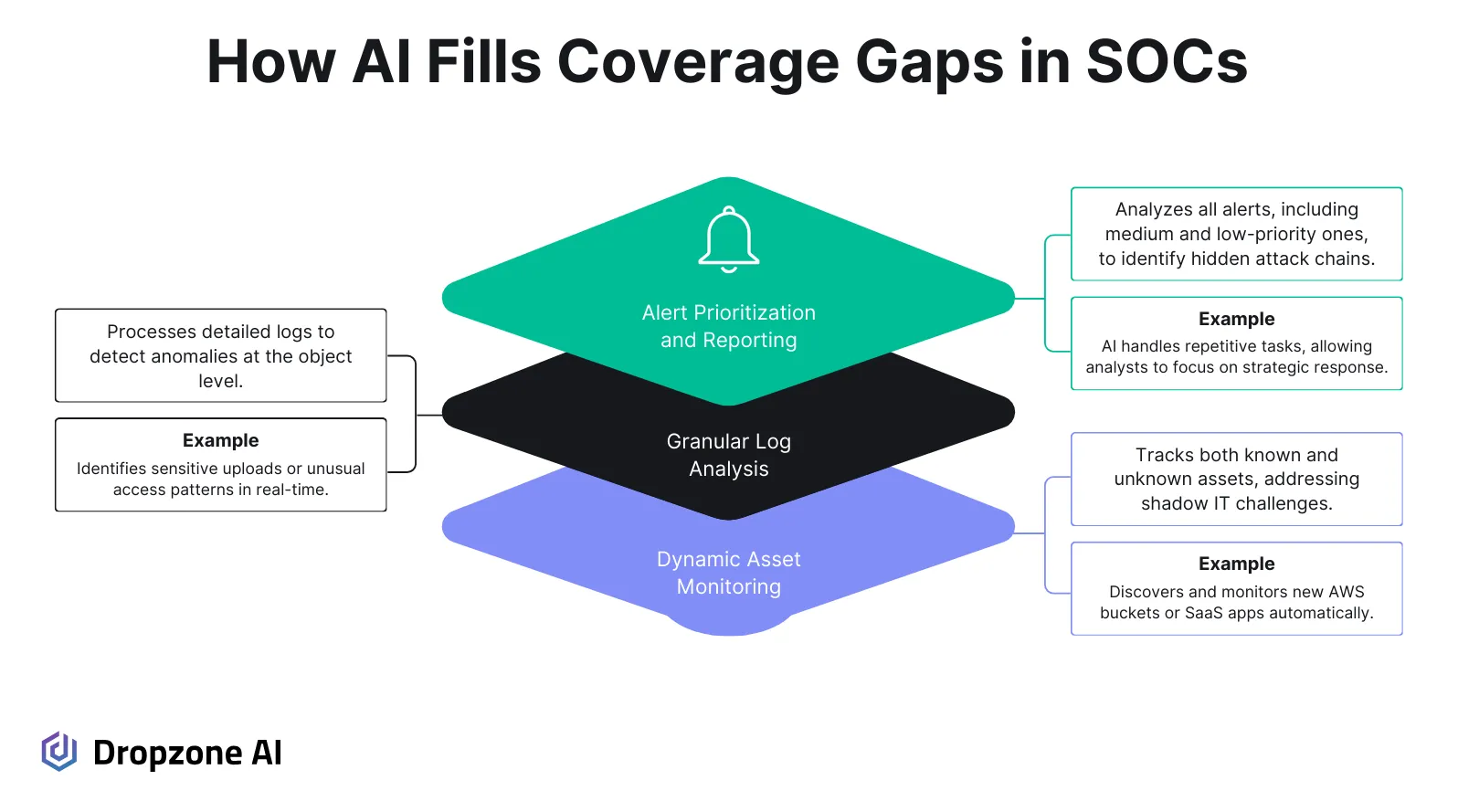
Asset and Credential Monitoring
Shadow IT remains a constant challenge for SOC teams, as unmonitored assets like forgotten AWS buckets or rogue SaaS applications are outside the visibility of standard tools. Future AI agents can follow conversations in internal systems like Jira or Slack, and understand when resources will be created or when credentials are shared. They could help the security team keep track of activity, or perhaps suggest secure practices for those activities in the context of the Jira or Slack conversation. This kind of automated discovery would reduce the risk of blind spots and ensure that every asset, intentional or not, is accounted for in real-time.
Granular Monitoring at Scale
SOC teams often struggle to keep track of ordinary system logs that could indicate malicious activity. AI in threat detection products could address this by combing through detailed logs at scale. This type of monitoring would prove especially useful at detecting insider threats and fulfill the promise of User and Entity Behavior Analytics (UEBA), which to date has shown promise but is complex to deploy and often generates too many false positives.
AI can address these deficiencies with more accurate detection. For example, if a SharePoint folder is shared with an external alias, an AI system would be able to search through emails and read through the communication history with that alias to determine if the resources were shared justifiably.
Triage for Every Alert
One of the biggest frustrations in a SOC is dealing with alert overload. Medium and low-priority alerts often get deprioritized because teams don’t have the time or resources to investigate them all. This is where AI makes a real difference.
AI SOC analysts investigate every high, medium, or low alert without losing focus or becoming overwhelmed. Caleb Sima summed it up during his BSides talk, asking the audience to imagine what is possible with AI agents, “What would you have 10,000 smart junior security engineers do?” AI SOC analysts essentially deliver that scale, investigating every single alert thoroughly to catch malicious activity that would otherwise go unnoticed.
To expand on this, consider how many medium-priority alerts may seem unrelated at first glance. An AI system can link these alerts and identify them as part of a larger attack chain. For example, it might detect a series of low-severity access anomalies across different systems that, when linked, reveal a coordinated attempt to gain unauthorized access. Without AI, these connections are easy to miss, leaving the SOC vulnerable to hidden threats. AI doesn’t just process more alerts; it helps SOCs understand the bigger picture, even with limited resources.
AI as a Human Analyst’s Trusted Teammate, Not a Replacement
Rather than replacing analysts, an AI SOC analyst is a trusted teammate, handling repetitive tasks like triaging alerts, gathering logs, and performing initial analysis. This frees analysts to focus on more proactive security tasks, like threat hunting or improving visibility by configuring logging.
Instead of spending hours digging through hundreds of raw alerts, human analysts can start with a full report highlighting key findings and showing its work, including raw evidence. This partnership between AI and analysts saves time and empowers SOC teams to work smarter and focus on tasks that require human expertise.
Conclusion
Coverage is central in making SOCs more effective by helping detect and respond to threats that might go unnoticed. AI enhances this by identifying shadow IT assets, providing detailed visibility into activity, and handling high volumes of alerts, freeing analysts to focus on tasks that need their expertise. This isn’t replacing SOC analysts but helping them work faster and smarter. If you want to see how AI can transform your SOC, watch the podcast with Caleb Sima and Dropzone AI Founder Edward Wu or explore the Dropzone AI demo gallery.















